This blog is based on the published study “Zero Trust Architecture: Next-Generation Cybersecurity Framework for Digital Enterprises” developed by Frost & Sullivan’s Growth expert, Heena Juneja from the TechVision ICT team. The content consolidates strategic imperatives, technology enablers, regulatory drivers, and companies to action that are accelerating ZTA adoption across global industries.
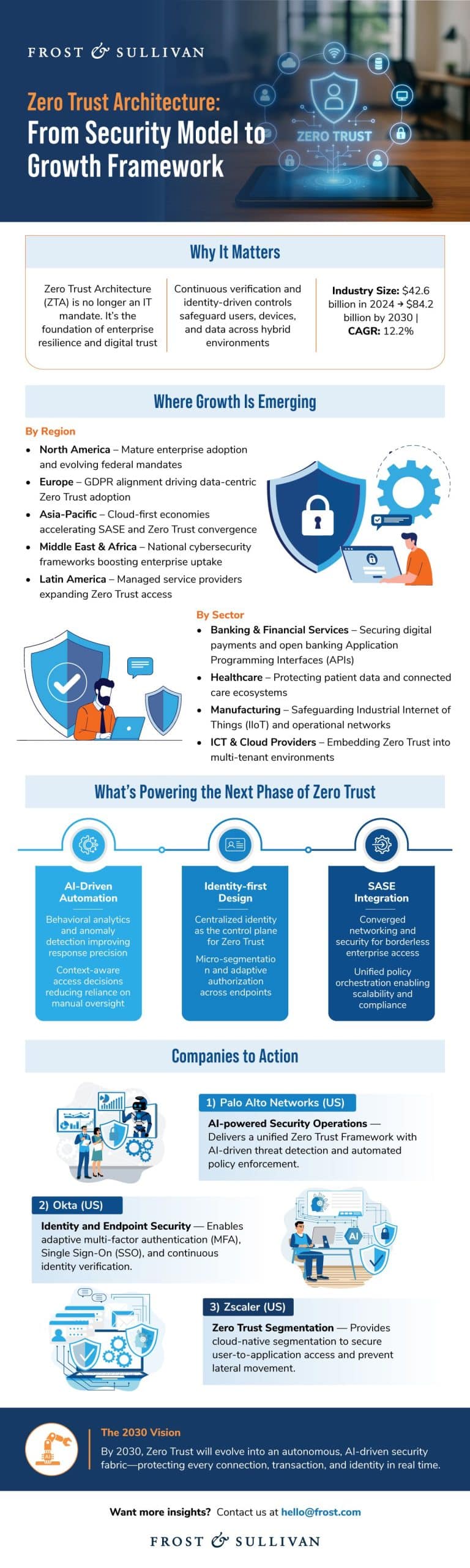
Enterprises navigating cloud expansion, hybrid work, and distributed networks face one unavoidable reality: the attack surface keeps widening. Traditional perimeter-centric security models no longer offer the control or visibility required to manage today’s complex digital ecosystems. Zero Trust Architecture (ZTA) has emerged as the most compelling pathway to modern resilience, guided by the core principle of never trust, always verify. It supports identity-driven access, continuous authentication, and strict segmentation across users, devices, and applications, which are positioning itself as the growth framework for cybersecurity in the coming decade.
The Zero Trust Evolution Roadmap Through 2029
Top Growth Opportunities: AI-orchestrated ZTA, decentralized trust models, and autonomous cybersecurity ecosystems. Is your roadmap ready for the shift toward self-healing Zero Trust models? |
|
Zero Trust aligned with National Institute of Standards and Technology (NIST) 800-207 and Secure Access Service Edge (SASE) gives enterprises the ability to scale security with agility while managing growing threats and compliance pressures. As organizations rethink their security posture, they are increasingly asking how Zero Trust accelerates operational continuity, improves risk visibility, and builds digital trust across ecosystems.
Explore Frost & Sullivan’s Sample Zero Trust analysis or connect with our cybersecurity strategists to assess your readiness at [email protected]
Identity Intelligence and AI: The Operational Core of Zero Trust
Identity and AI-driven decisioning form the heart of ZTA maturity. Identity intelligence acts as the digital passport of the Zero Trust ecosystem—verifying users and devices, enforcing least-privilege access, and continuously monitoring behavior for anomalies.
Identity as the Foundation
- Multi-factor authentication (MFA) mitigates credential-based attacks
- Access governance ties permissions to contextual signals
- Continuous monitoring validates real-time user behavior
- Use Cases: Google BeyondCorp Enterprise, Okta adaptive MFA and Single Sign-On (SSO)
AI as the Enabler
- Dynamic policy updates based on evolving behavior
- Early threat identification through automated anomaly detection
- Real-time risk scoring that adjusts access without degrading experience
- Use Cases: Microsoft Azure adaptive access, Zscaler AI-driven Zero Trust Network Access (ZTNA)
| Regulations Accelerating Zero Trust Adoption
Governments worldwide are embedding Zero Trust requirements into mandates and data-protection laws, pushing enterprises toward unified, compliance-driven security models.Key frameworks influencing adoption include:
These frameworks establish clear expectations for authentication, access control, and continuous monitoring, making Zero Trust essential for regulatory alignment. |
|
Growth Opportunity: Simplifying Cloud Security and Network Connectivity
With an opportunity size exceeding USD 1 billion in the next 3 to 5 years, the convergence of Zero Trust and SASE is transforming cloud-first enterprises. It enables secure, identity-driven connectivity across hybrid workforces, distributed applications, and global ecosystems. Regions such as North America, Western Europe, and Asia-Pacific are leading adoption across manufacturing, ICT, healthcare, BFSI (Banking, Financial Services, and Insurance), and government.
Unified, cloud-native security models reduce complexity, enhance policy enforcement, and support compliance at scale.
Learn how to position your organization for the next wave of Zero Trust and SASE-driven growth.
Ready to Lead the Zero Trust Transformation?
By 2030, Zero Trust and SASE will converge into unified security ecosystems that support digital trust and enterprise agility. Organizations that treat ZTA as a strategic framework—rather than a supplemental tool—will unlock stronger resilience, higher operational visibility, and accelerated business growth.
Get in touch with our TechVision ICT experts to explore customized Zero Trust opportunities, implementation strategies, and best practices tailored to your transformation goals.
Alternatively, you can write to us at [email protected].