Mounting Risks in Cloud Environments
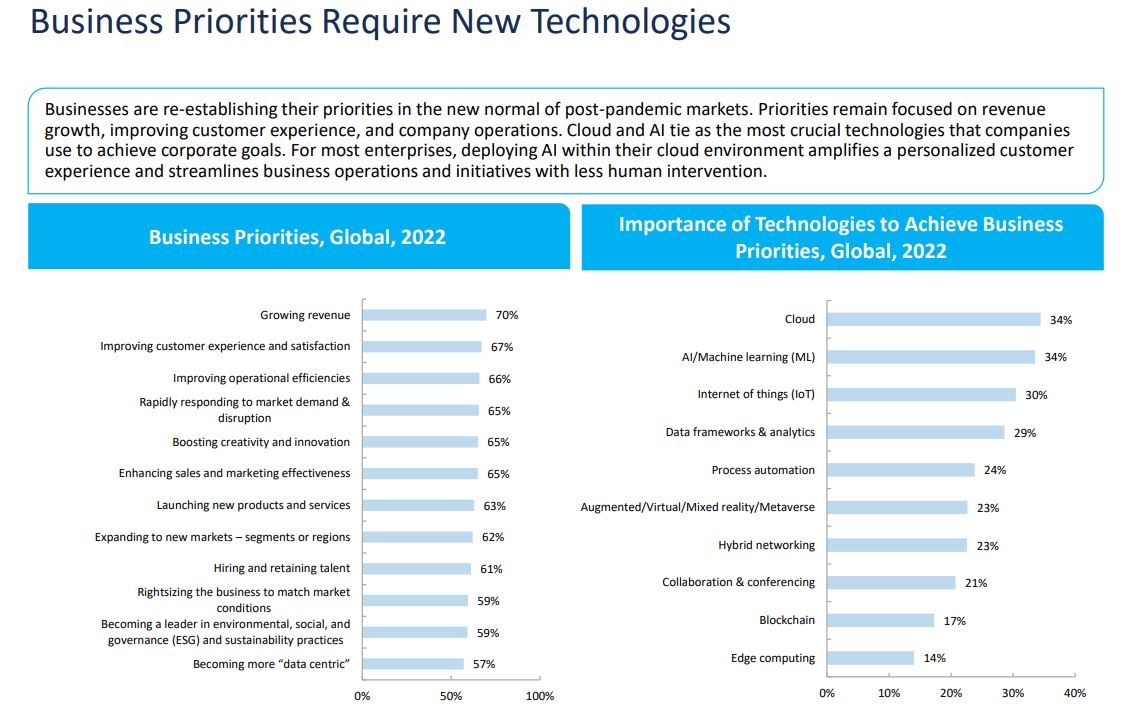
Organizations worldwide have been migrating to the cloud to help them achieve business goals of growing revenue, improving customer experience, and increasing operational efficiency. Recently, Frost & Sullivan surveyed nearly 1000 worldwide organizations and found that 73% of them see the cloud as the most important technology to achieve business priorities, among other technologies including Big Data Analytics, IoT, Collaboration & Conferencing, and AI/ ML. The survey shows that this movement is an inevitable trend that most organizations have been embracing with a majority already using public clouds and much more planning to migrate. Multicloud strategies are also becoming more common as companies seek to leverage the benefits of them.
The migration of workloads to public cloud environments exposes organizations to new attack vectors that were not present in on-premises data centers. As cloud services are increasingly adopted, the attack surface in the cloud environment expands and becomes more complex, leading to a variety of cyber risks such as insecure cloud connections, misconfigurations, identity and account theft, unauthorized access, and excessive permissions that pose unreverent security challenges for organizations. Over the last few years, there has been a drastic increase in the number of data breaches, service compromises, and violations or exploitations, such as cloud resource takeover and crypto mining.
American Financial, a provider of title insurance and settlement services to the real estate and mortgage industries, has taken measures to strengthen the security of its systems and protect its customers’ sensitive information. This includes the implementation of privileged access management, which restricts access to critical systems and data only to authorized individuals, reviewing, and updating its web pages to ensure proper authentication and authorization policies are in place. By taking these proactive measures, America Financial is committed to maintaining the highest level of security for its customers and preventing any potential data breaches.
Fidelity, an American multinational financial services corporation, strongly focuses and is committed to protecting their assets, applications, and data against cyber risks. To achieve this, it employs a Secure System Development Life Cycle (SDLC) process that includes formal security checkpoints throughout all stages of development. The company also implements security “DevOps” procedures to embed security checks into rapid development methodologies. In addition, Fidelity requires extensive testing and approval of all software before production deployment. All-access levels for all associates are reviewed annually, with high-risk systems and functions requiring additional approvals and more frequent reviews.
Hartford Financial is a United States-based investment and insurance company committed to cyber risk and access management with a strategy aligned with the NIST Cyber Security Framework. Regular cybersecurity updates are provided to the board and senior executives, and comprehensive data security policies and systems are assessed and tested annually by an independent third-party auditing company. The Hartford Cyber Center is a portal that offers access to resources, tools, and information on cyber security, risk mitigation, and breach response.
To curb cyber fraud and reduce operational costs, partially due to its decision to refund clients for fraud losses, Truist Financial is taking proactive measures to manage access and authentication. The company recently acquired Zaloni, a data management software start-up, to improve its data infrastructure in a hybrid cloud environment. It has also invested in security efforts such as identity authentication and fraud detection, as part of its technology spending to strengthen its IAM strategy by adopting the least privileged access principle.
The Fall of Legacy IAM and the Rise of Cloud-native Security Needs Cloud Infrastructure Entitlement Management (CIEM)
Cloud environments are vulnerable to cyber risks, oftentimes, due to excessive permissions and entitlements. Frequently, excessive permissions are attributed to technical debt and permissions debt incurred when organizations “lift and shift” workloads to the cloud. Consequently, organizations face a significant challenge in managing access permissions and entitlements for sensitive data and applications in the cloud. To reduce the risk of unauthorized access, data breaches, and other security incidents, they must prioritize permission or entitlement management. This involves only granting each identity and resource the necessary permissions and access for a specific task.
Traditional IAM solutions that are purposely designed to regulate access to applications and resources in traditional data centers are no longer adequate for managing access and entitlements in the cloud, which is highly dynamic and ephemeral. Additionally, cloud-native IAM tools provided by CSPs are not portable to other cloud service providers, making managing multiple providers a challenge. Organizations need a cloud-agnostic Cloud Infrastructure Entitlements Management (CIEM) tool to manage identity permissions and rights across cloud environments, enforcing access control policies and the principle of least privilege.
CIEM is the tool that provides capabilities to manage identity permissions and rights across cloud environments, allowing the team to enforce access control policy as well as the principle of least privilege. It automatically scans the cloud infrastructure configuration, access control policies, and rules, identifying vulnerabilities and misconfigurations and providing alerts and reports for fixing them before they are exploited.
To help organizations deal with permission and entitlement challenges in the multi-cloud environment as they are moving toward zero trust security architecture, Check Point, a leading cybersecurity company, offers a Cloud Infrastructure Entitlements Management (CIEM) solution – CloudGuard as part of its Cloud-native Application Platform (CNAPP). The solution provides unified visibility and control over access and entitlements across multi-cloud environments and helps organizations visualize, identify, prioritize, and remediate IAM risks and compliance violations, such as PCI DSS and GDPR across their cloud infrastructure. It enables organizations to optimize user and workload access and privilege management to enforce least-privilege access controls. CloudGuard uses machine learning and AI-based analytics to provide continuous monitoring of cloud environments, identify access anomalies, and detect suspicious activities that may indicate a potential breach.
With the increasing adoption of cloud services and growing awareness of security risks, data, and identity security have become critical components of cloud security strategies for global businesses. As they shift their focus towards improving identity security in the cloud, it is expected that CIEM will gain more prominence as a core element of CNAPP solutions moving forward. Therefore, organizations should consider adopting a cloud-agnostic CIEM solution such as CloudGuard, which provides comprehensive, automated, and AI/ML-powered capabilities to enhance their cloud IAM and zero-trust security strategy.