The internet from its first days in the form of Advanced Research Projects Agency Network (ARPANET) in the late 1960s to today has undergone a metamorphosis. It is a completely different beast now from what it used to be. The history of networking is short but extremely progressive filled with many breakthroughs. This rapid transformation in the underlying network has spiraled many businesses into higher orbits of productivity, profits & many a times into parlous territory. The pervasive use of digital technologies today in the form of cloud applications, distributed, and virtualized networks to create new business processes, products, and methods of consumption necessitate the breakthrough in cybersecurity as well. As the surface area of the network increased, it became increasingly complex for businesses to keep track of what is happening in the network.
To understand the problem further, we must take a closer look at how networks have evolved. One major change has been the explosion in the number of endpoints in an organization along with the disappearance of the network perimeter. IT and security teams today can no longer say, “This is where my network ends”. This has no doubt been exacerbated by the Covid-19 pandemic but has existed even before. In a survey conducted by Frost & Sullivan in 2021, roughly 60% of organizations with 500 or more employees now manage more than 10,000 endpoints. In parallel, the number of co-working spaces is expected to grow from about 19,000 in 2020 to more than 41,000 in 2024 according to Statista[1]. In essence the “corporate network” veil has disappeared for good.
How do you secure something which you cannot fully control?
According to industry research, 99% of cyberattacks traverse the network in some way2. As a result, networks become a treasure trove of information about past and future potential threats. 10 years ago, the market for Network Traffic Analysis (NTA) emerged which helped address the challenge of detecting threats from network flows. As the network traffic grew, organizations started adopting NTA as their go to tool to understand breaches. A market research study conducted in 2021, pointed that 43% of the organizations globally have deployed NTA3 as their first line of defense. However NTA was limited to studying network patterns and did not include a response aspect.
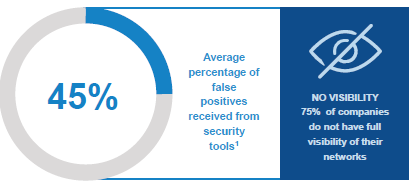
As network traffic grows, so do the correlation patterns and alerts to the security teams. Cyber criminals understand this fact more than anyone else. Cybercriminals hack human vulnerabilities more than the machines. According to a Frost & Sullivan study, 45% of alerts generated by security devices are false positives. For security analysts, this is a big pain point. As the number of false positives increase, the likelihood than an analyst looking at those alerts will miss a credible threat also increases. Security analysts are humans and can only take in so much data, before the noise takes over.
To minimize false positives, security technology has to upgrade from just log aggregation to enabling contextual and actionable insights into threat vectors. Security teams need full control and insight into the network before they can secure it. With advancement in machine learning, network traffic analysis technology has evolved into network detection & response (NDR)
The rise of Network Detection & Response (NDR) in Cybersecurity
The core of NDR is automated and adaptive cybersecurity. It takes network traffic metadata and uses machine learning and artificial intelligence to quickly identify threats and automate the response. It doesn’t depend on pre-defined signatures to detect threats but instead focuses on behavioral traits of the network data. This has tremendous value in solving the human problem in cybersecurity — not just how cyberattacks are allowed onto a network but how cyberattacks are missed once they are in the network.
NDR tools are built to monitor network traffic in real time and have the ability to create a baseline and raise alerts when they detect an anomaly. These tools can gather data from multiple sources, most commonly – Netflow, DNS, firewalls, IDS/IPS, proxies and others across the IT & OT network. They become powerful and useful for the security analysts in the organization as they can track not just north south traffic across the enterprise but also east west traffic through network sensors. They can correlate this vast amount of data and can then provide both manual as well as automated actions to remediate any security incidents in real time. This not only reduces the human dependency but also reduces the Mean time to respond (MTTR) to security incidents. According to a 3rd party industry research the global NDR market is expected to grow at 17.5% CAGR from 2022 to 2026.
Some of the key cybersecurity vendors that are innovating in this domain are Lumu Technologies, Cisco Secure Network Analytics, Vectra, and Extrahop among others. Since this is an evolving technology, to gain customer confidence, vendors like Lumu.io are offering a free tier service across small, medium & large organisations. Many of these vendors offer a wide range of response and orchestration options through a broad ecosystem of partners that they work with through APIs. By integrating with the existing SIEM and SOAR solutions, NDR can be a powerful tool to gain pan network-visibility of traffic, giving the control back to the security teams so that they are fully prepared when they detect an anomaly.
Conclusion
NDR will likely play a larger role in organizations’ security postures in the near future. NDR’s synergies with Endpoint Detection & Response (EDR), Security Incident & Event Management (SIEM), and the emerging Extended Detection & Response (XDR) segment puts it in a good spot to be considered for future security decision-making. However, it is imperative to be cognizant that NDR is not a cure-all solution and is only as valuable as the underlying capability of AI and ML. Current market players are aggressively working to differentiate themselves with superior correlation & machine learning capabilities. It promises to be an exciting space to keep an eye on.
Should you have any queries on the NDR, EDR, XDR & other emerging technologies, or need more information or would like to schedule an interview/interaction with our authors, Vinay Biradar, Principal Consultant – Cybersecurity or Qi Yong Lim, Consulting Associate – Cybersecurity, please email Li Ping at liping.chwa@frost.com
1 Number of coworking spaces worldwide from 2018 to 2020 with a forecast to 2024, Statista, 2020
2 https://www.midlandinfosys.com/pdf/qradar-siem-cybersecurity-ai-network-analysis-wp.pdf
3 https://www.ibm.com/security/digital-assets/qradar/siem-ndr-better-together/